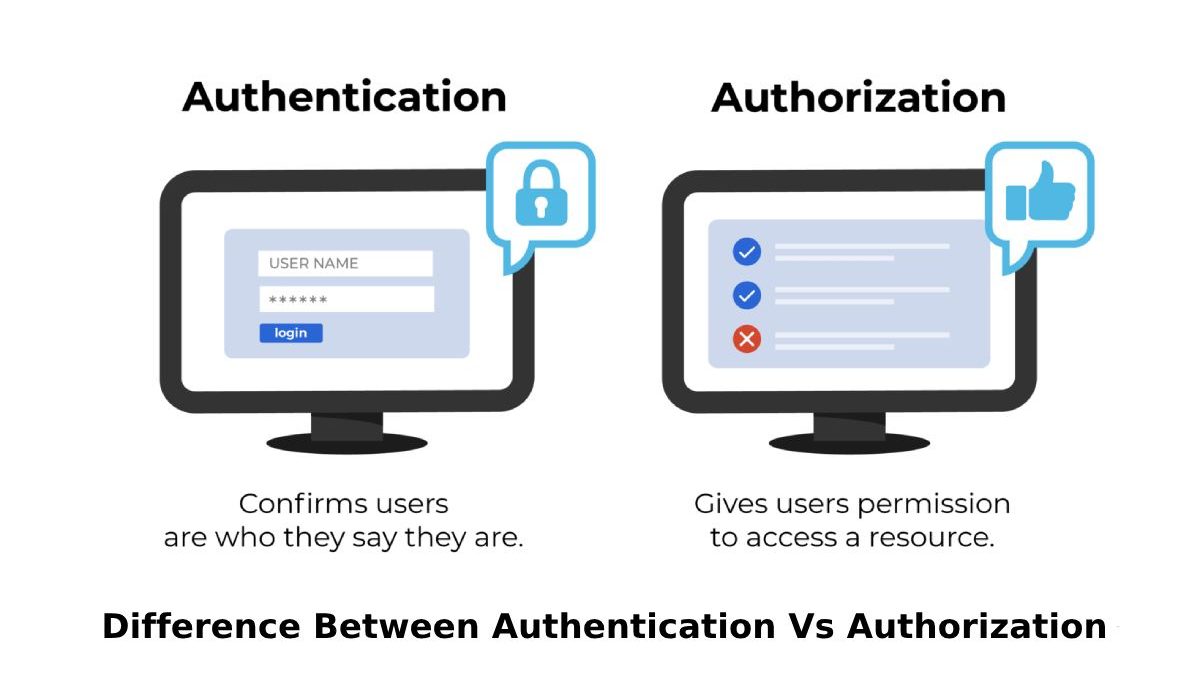
Authentication is used to verify the identity of a user, while authorization is used to verify the access permissions that a user has to specific resources.
Both work together to confirm that authorized users can access the appropriate resources. Authentication can be used to make authentication decisions.
For example, if a traveler checks into a hotel or restaurant, authentication is a security method that confirms they are who they say they are. Authorization is the procedure of determining the level of access granted to each user.
Authentication can verify identities through different methods, such as what we know, have, or have.
Table of Contents
What is Authentication?

Authentication is one of the many cybersecurity processes a company uses to protect its assets. The goal is to guarantee the user’s identity before granting access.
With authorization, users are allowed to access certain features or information. This security layer grants access privileges to employees while controlling access to crucial resources.
A company must provide authorization when a remote worker, employee, or customer needs to receive access to a specific application or file. For example, a company may require its employees to have permission to download particular files from the company server but would like to restrict their access to more sensitive financial files.
As another example, a company may want to allow individual users admin access to an end- point application, such as a content management system or member portal. Companies may also want to use authorization to restrict specific users’ access to sensitive data.
How Does Authentication Work?
Authentication works like a main in a locked door. Users must prove who they are to be granted access. Authentication can be granted using login credentials, such as:
- Usernames and passwords
- Unique Pins and Access Tokens
- Security Questions
- Authenticator apps that trust a phone number or email
This process can include everything from simple two-factor authentication to biometric, adaptive, and more secure multi-factor authentication: fingerprint or eye scan. Once the user is verified, the system grants access and unlocks that door.
What is Authorization?

While authentication is the key that allows a user to enter the door, authorization requires establishing layers of cybersecurity to open or restrict certain areas once the user passes that door.
With authorization, users are allowed to access certain features or information. This security layer grants access privileges to employees while controlling access to crucial resources.
A company must provide authorization when a remote worker, employee, or customer needs to receive access to a specific application or file. For example, a company may require its employees to have permission to download particular files from the company server but would like to restrict their access to more sensitive financial files.
How Authorization Works?
When creating a secure environment for a company’s network, applications, and data, authorization should come immediately after authentication. Once user accounts are validated, company administrators move them to the next level of security by allowing the user to access only the correct resources.
Authentication vs. Authorization
Many authentication systems, such as two-factor authentication, are available on the market. Likewise, there are many types of authorization available for businesses. However, business leaders often believe they must choose one of two options: authentication or authorization.
The truth is that both go hand in hand. Authentication confirms that users are who they say they are, validating the user’s identity. Authorization gives authenticated users permission to access a resource. Combined, they strengthen all entry points into your business, ensuring all data remains protected.
With LastPass, your company can leverage authentication and authorization policies to create a complete identity solution.
Authenticate and Authorization without Passwords
| Authenticate | Authorization |
| Incorporate biometric and contextual authentication factors to protect your business better. | Offer customization to leverage numerous MFA methods for access control at the user or group level. |
| Provide employees, remote workers, and customers with a password-less authentication user experience. | Provide a centralized list of granular policies to control access rights at the individual, group, and organization levels. |
| Seamlessly authenticate users across devices to maintain workflow and productivity. | Save time and money with a simple implementation process that requires no professional services. |
| Secure all access points, from cloud and on-premises applications to VPNs and workstations, for successful authentication. | Automate provisioning with user directories like Microsoft AD and Microsoft Azure AD with easy setup and minimal management. |
| Ensure biometric data is encrypted at the device level and remains on the user’s device for added privacy and security. | Provides multiple authentication protocols and authorization plans to fit each company’s size, security needs, and budget. |
Conclusion
Authentication and authorization are two key security measures that work together. Authentication verifies the user’s identity (such as verifying their ID), while authorization determines what actions they can take (such as showing their boarding pass). Together, they ensure that only authorized users access specific resources. Imagine needing a key card to enter a building (authentication) and your specific floor (authorization). A secure system requires both.
Related posts
Featured Posts
Artifact – Brief Explanation
What is an Artifact? An Artefactos, also known as an Artifact in English, is an object, machine, or device whose…
Web Server – Brief Explanation
About Web Server Web servers are programs (software) used daily on the Internet. They intermediate between the server on which…